Customer Protection Comes First
AVICII understands that cyber threats are ever-present and move fast. At AVICII, we invest significantly in our team, tools, education, and industry partnerships, all with one mission: to help keep our guests’ information secure.
Throughout, this site you will find tips to help you protect yourself from activities used by threat actors, as well as information about how to take action when it comes to your security concerns.
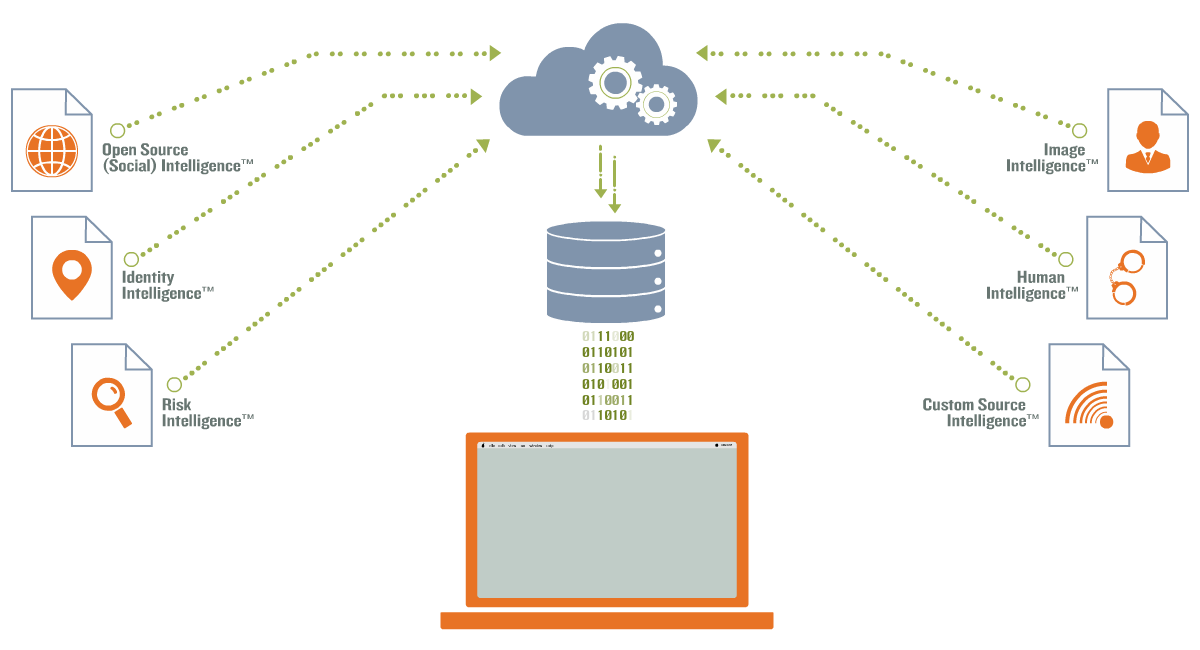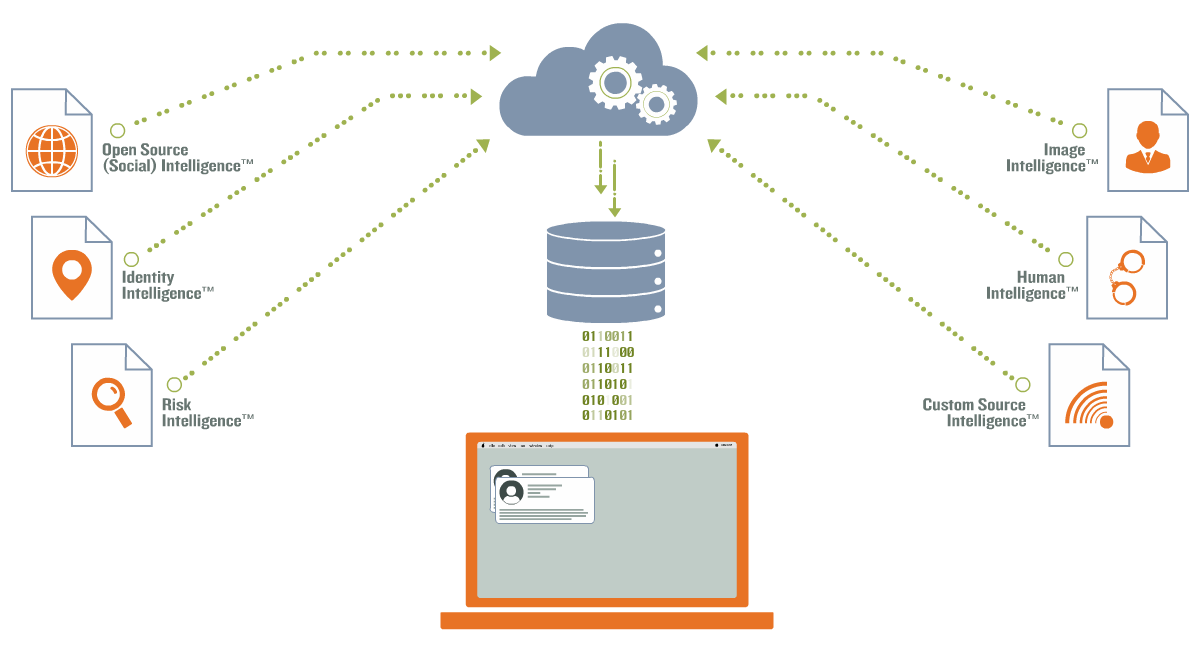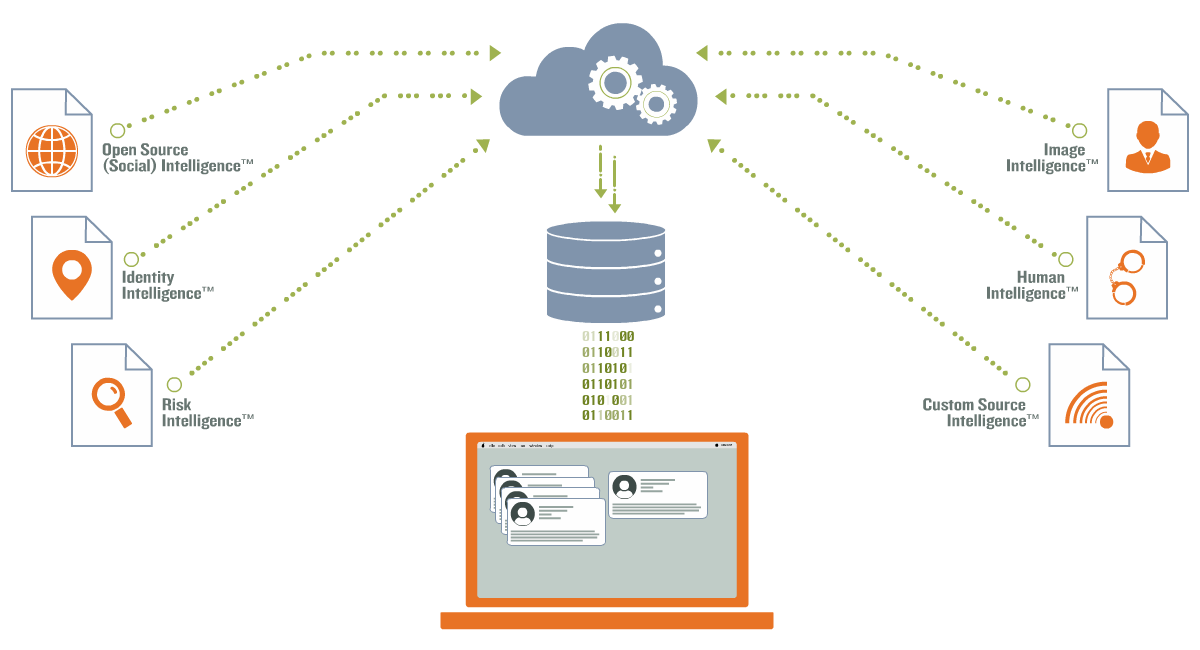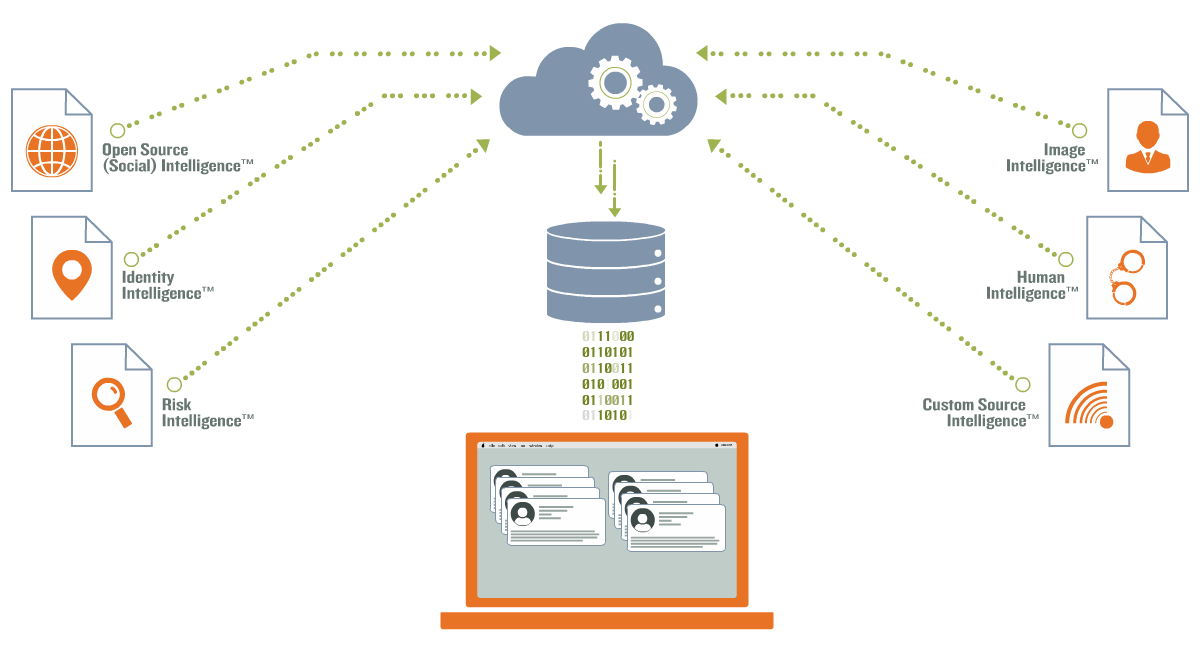 Identity Protection Scan Flow-map:
@
Identity Protection Scan Flow-map:
@
Information security measures are taken to protect the privacy of your information, preventing unauthorized access to accounts, passwords, viruses, hackers, websites, and databases. False IP is immediately detected. We keep our website up to date, SQL injection, XSS, Server aid validation, File upload, SSL, website security tools. We use SSL (Secure Sockets Layer) protocol, which transforms your data into an encrypted code that cannot be read during transmission. AVICII uses a firewall to filter and prevent any unauthorized attempts. We choose to make everything about your usage and information private.
Get in the habit of using different, strong usernames and passwords for all accounts.
It is important to use a different password for each of your accounts, even though it’s difficult to remember them all. When you use the same password for multiple sites where you shop or log in, one incident at any of those places leaves you at risk everywhere. Make sure to avoid using really obvious or easily guessable passwords (such as 123456 and password1234).
Keep track of all the sites that require you to use your email address as the user ID at login. Make sure that your email account has very strong security and recovery information that is hard to guess and unique from all your other accounts. Finally, never share your passwords and pins, and change your passwords and pins frequently. One easy way to manage multiple, complicated passwords is to use a password manager or vault.
Don’t use passwords and switch to passphrases.
Another way to come up with a memorable, ironclad password is to use a passphrase, a series of numbers, letters, and symbols that stand for an easy-to-remember line or phrase. They’re longer and more secure, and you’re more likely to remember a sentence than a word. For example why go to the beach when it’s raining? = YGo2tBwit$r@ining?
Don’t just click on a hyperlink. Test it out first.
Another tactic that Intruders use is to attempt to get you to click on a hyperlink in an email or online ad that looks like it will take you to your favorite shopping site but leads to an illegitimate one. Before clicking on any links, hover over them to see the full URL and make sure you know where the link is taking you. If you’re not sure it’s safe, don’t click on the hyperlink. Use a web browser to navigate to the brand’s trusted website instead.
Be on the lookout for red flags in every email.
Intruders take advantage of busy times when people are more likely to be receiving confirmation and shipping emails, promos for deals, and more digital goodies. They create phishing emails that appear to be from your favorite brand to catch you off guard. But if you look closely, some features will tip you off that something isn’t right. For example, they usually come from a slightly “off” email address that’s different from the company’s official handle. Misspelled contacts and brand names, typos and bad grammar are also big red flags. So before opening, ask yourself: Am I expecting this email? Do I recognize the sender’s email address and is it spelled correctly? If this email references a company I shop for, does it come from the company itself?
AVICII Gift Cards can only be used at AVICII stores and on AVICII.com, and cannot be used to purchase other prepaid or specialty gift cards. No legitimate government entity, including the IRS, Treasury Department, FBI, or local police department, will accept any form of a gift card as payment. Do not search your gift card balance within search engines.
Since it is common for threat actors/fraudsters to request gift cards as payment, it is important to remember that other businesses or government entities do not accept payments in the form of AVICII GiftCards. For example, you will never be asked to pay your utility bills, bail money, debt collection, or hospital bills with AVICII GiftCards.
- Do not purchase, sell, or check your balance on online marketplaces outside of AVICII.ca
- If you get a call from a stranger who says that a loved one is in trouble and they ask you to provide gift card numbers to help them, hang up and contact your loved one directly.
- Do not purchase a gift card if it appears that the packaging has been altered or manipulated. If you have questions about a gift card, ask someone who works at the store.
- Do not click on or respond to online ads or websites offering gift cards. These are often scams.
Common Fraud Tactics
Phishing
When a threat actor/fraudster uses the AVICII brand to trick people to visit a fraudulent website that looks like an AVICII website. The victim is enticed to share sensitive information that the fraudster uses for the crime.
Phishing comes in many forms and sometimes looks like a legitimate communication from a retailer. The intention of phishing is always to get personal information from the victim, such as login credentials, identifying information, and financial information.
To protect yourself from phishing, remember to pause, keep calm, and be extra cautious when reviewing emails. To identify phishing emails, it’s important to remember while you may receive many legitimate emails, before clicking any links, validate that the sender’s email matches an email you’re expecting. If you have any doubt, don’t click any links and visit the site directly.
Vishing/Social Engineering via Calls
Combines “voice” and “phishing” and refers to a threat actor/fraudster using the AVICII brand to lure a victim into revealing personal information over the phone.
Often, fraudsters will mask their phone number to appear as if they are calling from a legitimate company. Do not always trust your caller ID. Intruders can manipulate a caller ID to look like a legitimate company or government agency.
Be suspicious of unexpected phone calls, especially ones claiming that you have won something, have an outstanding fine that you are unaware of, or the caller is claiming they are there to help you recover lost funds. If you receive one of these calls, hang up the phone and contact the reporting party directly.
Smishing
Refers to a threat actor/fraudster using the AVICII brand to lure a guest into revealing personal information via text message.
They will often offer a service or request a survey to get personal information from the victim, such as login credentials, identifying information, or financial information.
Similar to phishing, if you receive an unexpected text message with a link, you should be extra cautious and contact the reporting party directly to confirm its validity.
Common Gift Card Scams
Internal Revenue Service (IRS) / Government Scam
Intruders call and claim that they are the Internal Revenue Service (IRS), Social Security Administration (SSA), or another government agency and that the victim owes that agency money. Sometimes the Intruders say that the victim will lose their house or will be arrested if they don’t pay immediately. The Intruders then instruct the victims to purchase gift cards and give them the gift card numbers over the phone.
If you owe federal taxes or think you might owe taxes, hang up and call the IRS at 1-800-829-1040. IRS workers can help you with your payment questions.
If you don’t owe taxes, call and report the incident to the Treasury Inspector General for Tax Administration at 1-800-366-4484.
You can also file a complaint with the Federal Trade Commission at FTC.gov. Add “IRS Telephone Scam” to the comments in your complaint.
Computer Take Over Scam
In this scam, the scammer will pose as a representative from a bank or retail store that needs to access your computer or email to initiate a refund for overpayment by the customer. The customer provides access to their computer, bank account, or online retail account and the scammer subsequently steals gift cards and financial data from the victim.
Co-worker/Boss Scam
Intruders will send a text message masking the caller ID to appear as a co-worker or your boss and request gift cards for work or personal needs. The Intruders then instruct the victims to purchase gift cards and give them the gift card numbers via text message.
More information can be viewed at FTC: A Bossy Business Scam
The Grandkid Scam
In this scam, the scammer will pose as a relative or friend, calling a victim and indicating that a loved one is in some sort of trouble (e.g. kidnapped, arrested) Sometimes, the scammer even pretends to be the loved one or in a position that can help and asks directly for money. The scammer then instructs the victim to purchase gift cards and give the gift card numbers to the scammer over the phone.
Tech Support Scam (Computer/Helpdesk)
In the “Tech Support Scam,” Intruders will often pretend to be associated with Microsoft, Apple, or a cybersecurity-related company and say that their computer is infected and that they can help. These Intruders will often ask for remote access to your computer and will pretend to run tools on your computer that “discover problems.” These Intruders will then pressure the victim to pay them, often through the purchasing of gift cards. Sometimes this scam will be in the form of pop-ups or online ads that look like alerts on the screen.
Unexpected AVICII.com Order Email or Letter
The practice of requesting action by the recipient to either call or go to an email page to share personal information or take action such as deposit a ‘fake check’ or purchase something in exchange for a future payment. The intention could also be to get personal information from the victim, such as login credentials, identifying information, financial information, or more.
Mystery Shopper
Intruders send a check and letter to victims and inform them that they can make money as a “mystery shopper” for a retail store. They try to get victims to deposit fake checks, create a cashier’s check and buy items at the store. The fake check bounces after the guest have sent gift cards and merchandise to the scammer. The scammer may also use this tactic to attempt to get personal information from the victim. AVICII is not affiliated with any mystery-shopping firms or individuals.
What are some additional resources?
Contact the FTC, which handles complaints about deceptive or unfair business practices. To file a complaint, visit https://ftccomplaintassistant.gov/, call 1-877-FTC-HELP, or write to:
Federal Trade Commission
CRC-240
Washington, D.C. 20580
For updates on other types of potential scams, check out the FTC’s “scam alert” website at https://www.consumer.ftc.gov/scam-alerts.
For more information on imposter scams, check out the FTC’s imposter scams website at https://www.consumer.ftc.gov/features/feature-0037-imposter-scams.
At AVICII, we take security seriously. If you are a security researcher and would like to report a potential security vulnerability in any of AVICII’s guest-facing online services, please submit your information below for our security teams to review and investigate. We require security researchers to interact with us responsibly and by this Policy. If you conduct your security research and disclosure as authorized under this Policy and otherwise in good faith, AVICII will not take legal action against you related to such activities. AVICII reserves all of its legal rights in the event of any noncompliance.
AVICII will deal in good faith with security researchers who discover, test, and submit vulnerabilities or indicators of vulnerabilities by this Policy and is committed to coordinating with you as openly and quickly as possible. We will do our best to acknowledge receipt of your report within 7 days and may contact you for more information after we have begun our investigation. To expedite this process, please provide all necessary details for our team to fully reproduce your issue. To the extent that we are able, we will confirm with you the existence of any vulnerability and share with you any remediation steps taken by AVICII. After a vulnerability has been validated and fixed, we will seek to allow researchers to be recognized whenever possible. However, public disclosure of vulnerabilities will only be authorized after the vulnerability has been addressed and requires the express written consent of AVICII. In the event the report you submit involves a third-party vendor, we will forward your report to that vendor. AVICII does not offer monetary rewards for vulnerability submissions.
Engaging in any of the following activities is a violation of this Policy:
- Publicly disclosing the potential vulnerability without AVICII’s consent
- Accessing any guest data or accounts other than your own
- Modifying, exposing, or exfiltration any guest data or accounts
- Compromising the privacy or safety of any AVICII guest or team member
- Compromising the intellectual property of AVICII
- Testing any applications or services not owned by AVICII
- Performing or attempting to perform denial of service or other attacks that degrade AVICII operations
- Utilizing malware or other malicious software in any way
- Testing in a manner that would result in sending unsolicited messages to guests or team members
- Submitting a high volume of low-quality reports
- Submitting reports to AVICII through any method other than this form
- Submitting low-severity issues with no clearly defined security impact
- Failing to immediately delete/destroy sensitive information you may inadvertently access
- Researching by physically connecting to an AVICII network or other device within an AVICII store or AVICII property
- Researching social engineering or other deceptive techniques
AVICII may modify or terminate this Policy at any time. Please review periodically to ensure you understand the current Policy.
Submit Information Here:
Please send details of the security vulnerabilities by sending us an email with the following information:
- A clear description of the issue
- Full URL where discovered
- Steps to reproduce the issue
- Attachments
- Recommendation(s) to resolve the issue(s) if known


